Activist and peer led sites
Infrastructure for lived experience projects and grassroots campaigns that run on limited capacity but attract big reactions.
See activist sitesIf you are running a peer led advocacy project, a grassroots campaign, a survivor support network, a reform effort, or any other public interest platform, your site needs to be stable, resilient, and technically clean.
I help with the platform, not the message. Neutral infrastructure only. You control what you publish, I make sure the site stays online when attention hits. I am based in the North East and work UK wide. If you are in the region and want local context or hands on support, there is a dedicated North East track below.
The same technical stack, tuned for different kinds of high risk work.
Infrastructure for lived experience projects and grassroots campaigns that run on limited capacity but attract big reactions.
See activist sitesStatic builds, Cloudflare setups, and logs for work that scrutinises contracts, public bodies, and serious institutional failure.
See anti corruption focusLocal accountability projects watching councils, housing providers, contractors, and services that usually go unscrutinised.
See watchdog sitesGuidance pages, secure contact routes, and hosting patterns that support whistleblowers without overpromising safety.
See whistleblower workCampaign sites and rapid response pages built for pile ons, doxxing attempts, and sudden attention from all sides.
See campaigner safetySimple, explainable protections for charities, CICs, mutual aid groups, and small organisations that sit in the firing line.
See NGO securityStatic architectures for high risk work, so you are not depending on a fragile CMS when attention spikes.
See static buildsCloudflare logs, timelines, and exports that can sit in complaints, internal reviews, and regulator correspondence.
See logging offerRules, rate limits, and fingerprint aware defences that keep search engines happy while hostile automation pays a price.
See bot mitigationKi-Ki works UK wide. These pages exist because public interest work is often local first, and people search locally when they need help fast.
If you are in the North East and building an advocacy site, watchdog project, campaign page, or whistleblower safe platform, you get the same stack as everyone else plus optional local context, faster on site collaboration when needed, and a regional understanding of how attention lands here.
Outside the region, the offer is identical. The difference here is simply local availability.
You do not need a large team or a formal organisation to need serious infrastructure.
Groups built around lived experience, mutual support, or survivor led community work.
Local or national movements, reform efforts, and issue focused organising.
Sites focused on accountability, scrutiny, or documenting systemic failure.
Citizen journalists, watchdog blogs, whistleblowers, and small teams publishing uncomfortable truths.
If your work is lawful, serious, and likely to attract attention, it belongs here.
Fast, predictable builds that do not depend on bloated plugins or fragile admin panels. Good for projects that need clarity and uptime.
See Secure static sites.
Firewall rules, rate limits, bot mitigation, Workers, and clean routing, tuned for the kind of traffic public interest sites attract.
Edge level traffic logging, challenge events, and timelines you can take to trustees, regulators, platforms, or supporters.
For projects likely to face quiet institutional or adversarial attention, I set up lawful fingerprinting on your own domain so repeat devices and patterns are visible.
SPF, DKIM, DMARC, DNS records and deliverability, so your comms do not disappear into spam at the worst moment.
If you handle sensitive tips or lived experience accounts, I can set up secure PGP based contact so people can reach you safely.
See Secure PGP contact.
Quick fixes to privacy notices, retention, consent handling, and SAR processes, so your policies match how you actually operate.
If your service includes limited SEO or baseline site copy, it stays neutral, factual, and only goes live after written approval from both of us.
High attention sites are magnets for hostility, takedown attempts, and random nonsense.
Neutral infrastructure keeps roles clean. I handle the technical foundations and keep the platform solid. You handle your message, your publishing decisions, and your legal advice.
Public interest work attracts attention from institutions, contractors, competitors, and invested individuals. Sometimes it is open. Often it is quiet.
I build for that reality. Your platform is set up to anticipate monitoring, pressure, and low effort nonsense, and to stay stable while it happens.
The aim is not guesswork. It is evidence you can stand behind.
Full detail, examples, and the legal position are here: Fingerprinting and Edge Tracker.
Everything here stays lawful and defensive. We only fingerprint devices that connect to your own site, for security and evidence purposes. It identifies recurring devices and behaviour, not real world people by name.
I do not help anyone break the law. I help underdogs even the playing field against larger adversaries, with infrastructure and receipts that hold up when challenged.
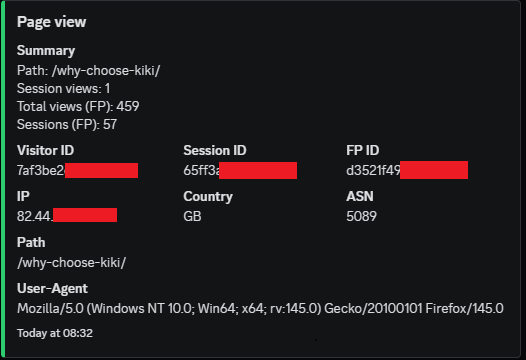
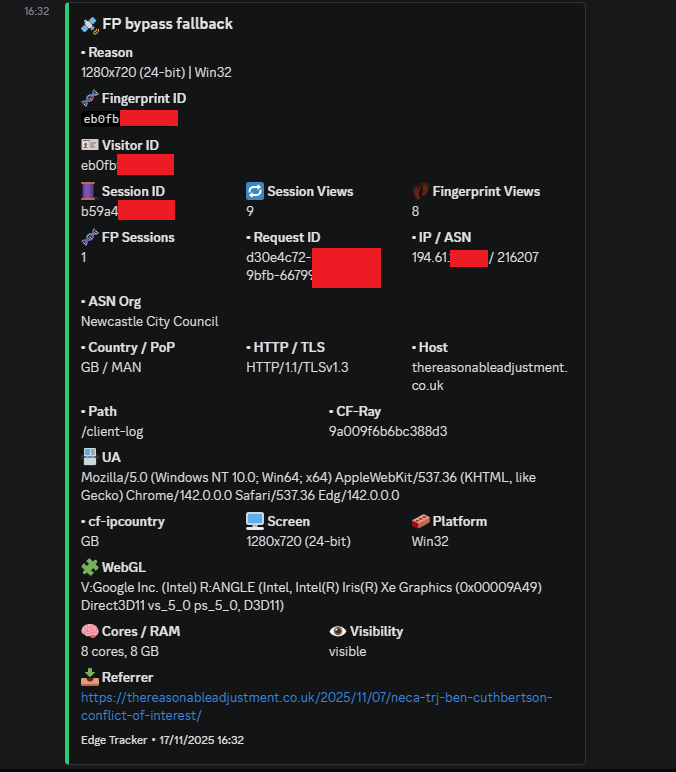
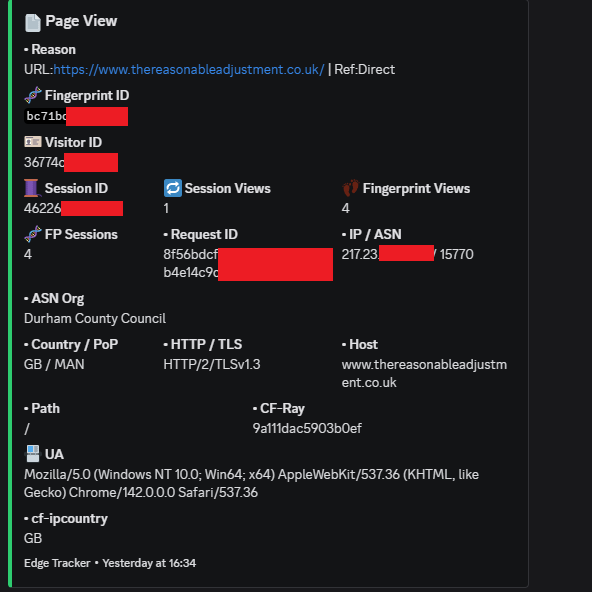
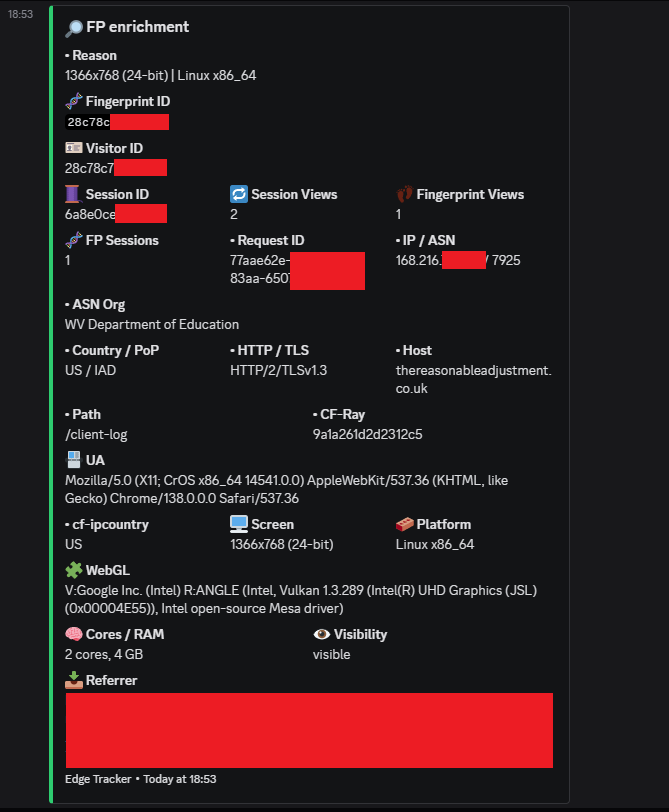
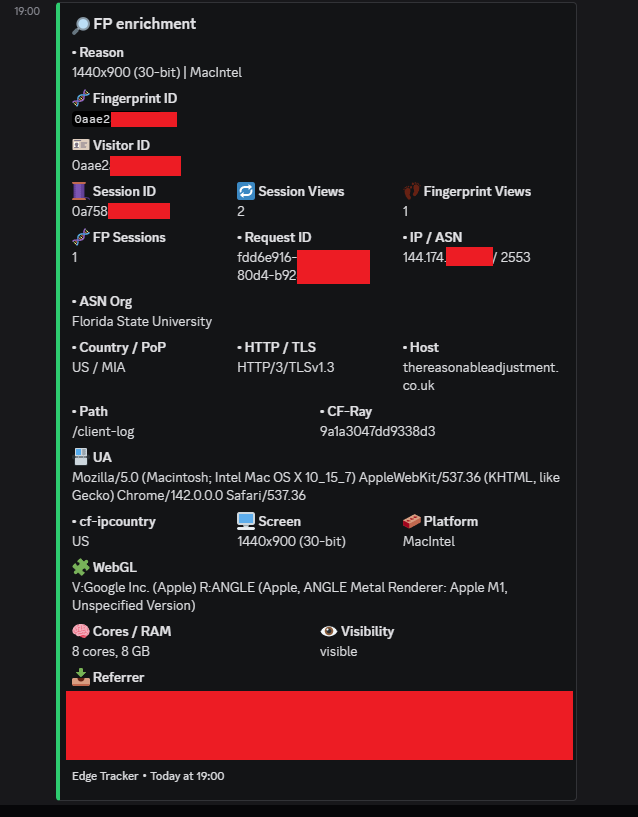
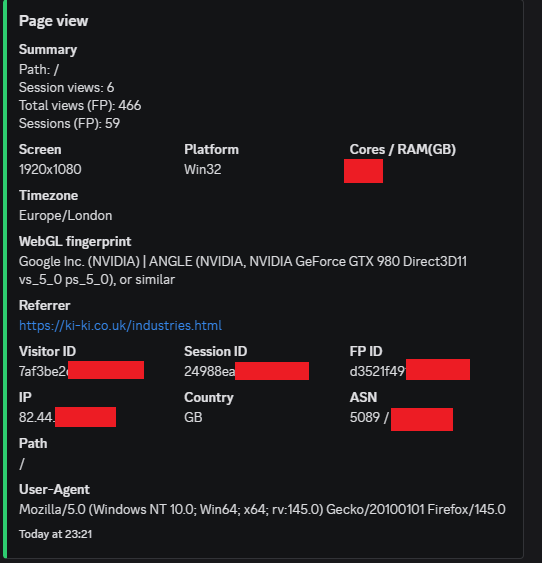
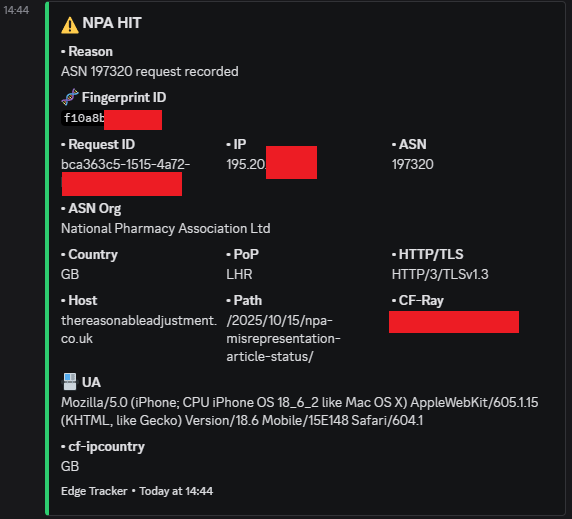
Below are redacted examples of Edge Tracker in real-world use. They show normal device logging, repeat actor detection, council network access, international education networks, and a case involving the National Pharmacy Association.
What these examples demonstrate:
Many organisations deliberately limit how much their devices can be tracked online. They may block cookies, rotate IPs, or use hardened builds that reduce fingerprint visibility. This is often policy driven security rather than malice. Edge Tracker treats that as background behaviour.
The National Pharmacy Association example is different only because there is a clear written denial. The logged access itself is not a claim of wrongdoing. It is a factual contradiction, visible at ASN level.
Full context for the National Pharmacy Association case is documented here: National Pharmacy Association monitoring case study .
If you want a deeper explanation of how this works and why it stays lawful, read Fingerprinting and Edge Tracker.
If you want to see how I approach public interest issues, evidence, and difficult systems, my own advocacy work lives here:
That site is not a portfolio for clients, it is my own public work. It shows how I think, how I document, and how I keep things defensible.
These limits protect you and protect me. They are not negotiable after the fact.
The full position is set out in the Neutral infrastructure policy. Your use of this site is also governed by the Terms of use and Privacy policy.
No. Ki-Ki is infrastructure only. I do not draft, edit, approve, or publish allegations about identifiable people. You control your own content and you are responsible for it.
It means I keep your platform stable, secure, and defensible, without taking a role in your message, targets, or legal strategy.
It lets you identify repeat devices and behaviour on your own domain, even when IPs change. That gives you patterns and evidence rather than guesswork.
Yes, when it is defensive, limited to your own site, and disclosed properly. I set it up that way and align it with your policies.
Yes. I can set up a PGP based secure contact route so sources can reach you safely. Details are on Secure PGP contact.
That is normal for public interest work. I build with that expectation, and give you lawful tracking and logs to document repeat actors.
No. Ki-Ki works UK wide. The North East pages exist for local search and for clients who want optional local context or in person support. The technical offer is the same everywhere.
You outline your project, what you need technically, and what level of attention you expect. I confirm scope and boundaries up front.
I set up the site, Cloudflare, email basics, fingerprinting if needed, and logging. You supply and publish your own campaign content.
You get a clear system map, action notes, and the option of a light retainer if you want ongoing protection.
Tell me what you are building, what worries you, and what level of attention you expect. I will tell you plainly whether I am the right fit.