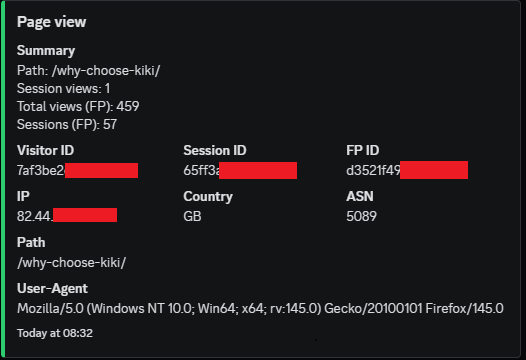
Baseline fingerprint record
Stable IDs, ASN, device profile, and referrer trail. Enough to link repeat behaviour across weeks.
Quick translation before we go any further. This is not a “criminal fingerprints” thing. In web terms, fingerprinting means building a stable device signature from technical signals when someone connects to your site.
Think of it like a quiet security camera for your website. It does not identify a person by name. It identifies recurring devices and behaviour patterns, even when someone tries to hide behind new IPs or VPNs.
If a device connects to your site, it gets fingerprinted at the Cloudflare edge. No cookie theatre, no front end scripts you can dodge, no hoping the browser plays along.
Every connecting device is assigned a fingerprint ID, visitor ID, and session ID. This lets us link repeat behaviour over time, even when users rotate VPNs or clear cookies.
We enrich each hit with ASN, network owner, country, and PoP. Where an organisation owns its own ASN, we can show traffic from within their internal network. Where an ASN is shared, we log it as an institutional group and rely on patterns to narrow the picture.
WebGL renderer, screen size, platform, cores, RAM, browser family, and other metrics give a stable signature. When someone tries to hide behind new IPs or browsers, the device still shows its hand.
The Worker flags patterns like bypass attempts, repeated visits to sensitive paths, sudden interest spikes, or recurring devices that keep reappearing after blocks. You get a heads up early, not after the mess lands.
Fingerprint counts, session counts, referrer trails, and page sequences build a lawful behaviour profile for any recurring actor. This is how you separate random noise from invested attention.
Redacted screenshots and structured exports that can be attached to internal reviews, safeguarding write ups, complaint responses, or legal letters.
These are cropped and redacted from live Ki-Ki stacks. The point is the structure and signal, not naming individuals.

Stable IDs, ASN, device profile, and referrer trail. Enough to link repeat behaviour across weeks.
The system flags attempts to avoid normal fingerprint routing. That avoidance becomes part of the profile.
Direct organisational attribution where the ASN is uniquely held by a public body.
Not just “an IP in the US”. A specific institutional network, plus a stable device signature.
Fingerprint and session counts show recurrence, while hardware traits confirm it is the same device.
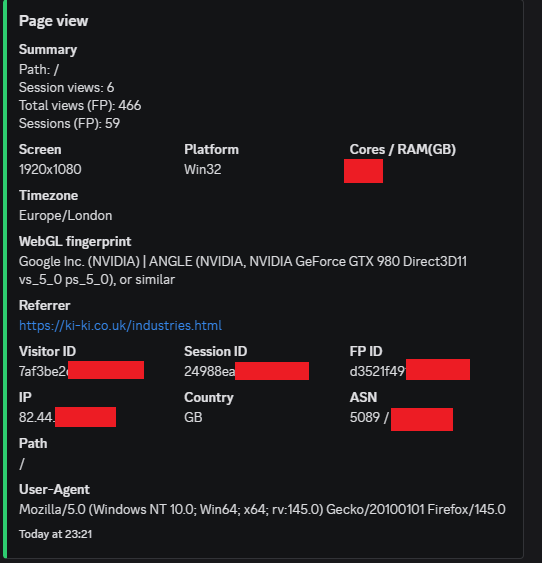
The default evidence block clients receive, including context for boards and governance teams.
The goal is accuracy you can defend, not guesswork you have to apologise for later.
When an invested party keeps returning, changing IPs rarely helps them. Devices are stubborn. Patterns are louder than people think.
This is useful for harassment patterns, targeted probing, quiet monitoring by public bodies, and competitors that want to look without being seen.
Early warning when a post starts attracting obsessive checking, harassment waves, or quiet institutional monitoring. See Content creator safety.
Evidence for governance, safeguarding, and disputes with funders or commissioners. Not guesswork, receipts.
Track probing, competitor interest, or recurring actors who keep circling sensitive pages.
Defensive logs that help you answer complaints properly, spot abuse, and show your board what is actually happening.
Fingerprinting is not a one size widget. Price depends on what you need and how deep the monitoring has to go.
One site, stable IDs, ASN enrichment, and clean evidence views. Good for most SMEs and charities.
For disputes, harassment patterns, or institutional monitoring. Adds evasion flags and suspicious activity alerts.
If you are unsure which level fits, start with a quick intake. I will tell you if you are overbuying.
You tell me what you are seeing and what outcome you need. We agree the depth of monitoring and retention.
I deploy the Worker and ruleset at Cloudflare, then validate signals and alert thresholds.
Traffic is fingerprinted, enriched, and streamed to your chosen channel. We watch for patterns that matter.
You get a clean evidence pack, plus options if you want to escalate, harden, or keep monitoring.
Yes. We only fingerprint devices that connect to your site, for security and evidence purposes. Data is minimised, scoped to your domain, and retained for an agreed period.
No. Fingerprinting builds a device and behaviour signature, not a real world identity. It is about recurrence and patterns, not naming people.
They can change IPs all day. Hardware traits and entropy patterns stay consistent, so repeat actors still show up.
Some ASNs are shared. In those cases we log attribution neutrally at ASN level, and use device and behaviour correlation to build a defensible evidence file without overclaiming certainty.
Tell me what feels off. Odd repeat visitors, suspected monitoring, harassment patterns, bots adapting to blocks, or a dispute you need receipts for.